Deciphering credit Card Numbers
|
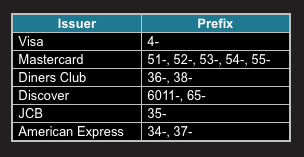
Credit cards, typically, have sixteen digits on the front. These digits are the unique account number for the card. For obvious reasons, just any sixteen digits will not work, they follow a specific pattern. The first few characters of the card number describe the type of card. Some of the most common card prefixes are summarised below
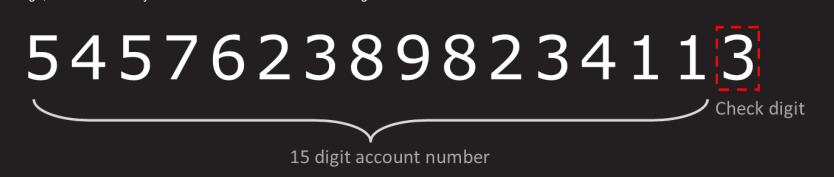
 In a typical sixteen digit credit card number, the first fifteen digits are determined by the issuing bank, but the last digit, called the check digit, is mathematically determined based on all the other digits. The algorithm was originally invented (and patented by by Hans Peter Luhn at IBM in 1954.
 |
If you have a Visa, Mastercard, or Discover Card number handy, do a Google search for the first 8 digits in the form "1234 5678" (don't forget the double quotes around the numbers, and the space in the middle). The odds are that you will find at least some pages among the search results which include other credit card numbers that begin with the same 8 digits. Those Google hits will frequently be in the form of a spreadsheet or document that looks like it was made for someone's internal use and wasn't meant to be leaked on the Web, and some of those documents will include entire lists of other credit card numbers as well. (The search trick doesn't work for American Express cards, since their card numbers are usually stored in the form "3xxx xxxxxx xxxxx", and it's far less likely for your card to share the same initial 10 digits with someone else's credit card. But of course if you hit on a page that contains a list of credit card numbers, there will probably be some AmEx cards in that list.) Of the pages that I found containing leaked credit cards, often they would also contain other sensitive data like passwords and social security numbers. Don't do anything I wouldn't do. |  |
The vast majority of the time, CVV data is harvested/stolen by web-based keyloggers. This is a relatively uncomplicated program that behaves much like a banking trojan does on an infected PC, except it's designed to steal data from web server applications. PC trojans like ZeuS, for example, siphon information using two major techniques: snarfing passwords stored in the browser, and conducting "form grabbing" — capturing any data entered into a form field in the browser before it can be encrypted in the web session and sent to whatever site the victim is visiting. Web-based keyloggers also can do form grabbing, ripping out form data submitted by visitors — including names, addresses, phone numbers, credit card numbers and card verification code — as customers are submitting the data during the online checkout process.